Subdomain Takeovers Exploits, Blind Spots, and Defend Your Digital Turf
In our previous post, we traced the decade-long evolution of subdomain takeovers from a niche issue to a widespread security risk with significant financial and reputational consequences. Now, we delve deeper into how attackers weaponize these vulnerabilities, why this threat is often underestimated despite its impact, and critically, what organizations can do to monitor for and mitigate this risk

🧠![]() Anatomy of an Attack: Real-World Subdomain Takeover Exploits
Anatomy of an Attack: Real-World Subdomain Takeover Exploits
Attackers leverage the inherent trust associated with a legitimate domain. Here are five common ways they exploit hijacked subdomains:
- Credential Phishing & Malware Delivery: This is perhaps the most common abuse. Attackers host fake login pages or malware droppers on the hijacked subdomain. Since the URL belongs to a trusted entity (e.g.,
support.yourcompany.com), users are more likely to fall victim. A researcher demonstrated this potential by taking overdata.teams.microsoft.com. In a large-scale 2024 campaign dubbed "SubdoMailing," attackers used over 8,000 hijacked subdomains from major brands (MSN, VMware, eBay, McAfee) to send millions of phishing emails daily that bypassed filters because they originated from legitimate domains (passing SPF/DKIM/DMARC).
- Cloud Resource Abuse & Data Exposure: When a subdomain points to a deprovisioned cloud resource (like an AWS S3 bucket or Azure web app), an attacker claiming it can potentially access leftover data or abuse associated permissions. One bug hunter took over an Uber subdomain (
mta1a1.spmail.uber.com) linked to their email system, gaining potential access to data scoped to that domain. In a sophisticated 2024 attack, Truffle Security took over a SaaS documentation subdomain (from ReadMe) used by multiple companies, allowing them to steal API keys and passwords stored in the browser's localStorage for that domain.
- Session Hijacking & Cookie Theft: If web applications set session cookies scoped to the parent domain (e.g.,
.yourcompany.com), an attacker controlling any subdomain (hijacked.yourcompany.com) can potentially read or set cookies for the entire domain. This can lead to account takeover. Researchers have demonstrated this against major companies like Uber (bypassing authentication by controllingsaostatic.uber.comused in the login flow) and Ubiquiti Networks (interfering with SSO by hijackingping.ubnt.com).
- Hijacked OAuth Redirects and SSO Flows: Modern authentication often uses redirects. If an OAuth
redirect_uripoints to a subdomain that becomes derelict, an attacker can claim it and intercept authentication codes or tokens meant for the legitimate application. This allows attackers to hijack login sessions, as seen in various bug bounty reports involving services like Salesforce or government login portals where partner subdomains were vulnerable.
- Hacktivist Defacements and APT Intrusions: Some attackers seek visibility. A Turkish hacktivist defaced a subdomain of the Joe Biden campaign website (
vote.joebiden.com) in 2020 after taking it over. Similar incidents have affected other political campaigns. More concerning is the potential for nation-state actors (APTs) to use subdomain takeovers for stealthy initial access or supply chain attacks, perhaps hosting malicious updates on a compromised supplier's forgotten subdomain.
❓Why Are Subdomain Takeovers Still Underestimated?
Despite the clear risks, many organizations historically underestimated this threat due to several factors:
- Stealth and Complexity: Takeovers exploit configuration errors, not code vulnerabilities. They bypass many traditional security controls (firewalls, WAFs) and can appear legitimate (valid DNS, HTTPS). Phishing emails sent from hijacked subdomains often bypass filters and user training focused on typos.
- Underappreciated Impact Breadth: Teams might dismiss a "minor" marketing subdomain, not realizing it can be used to set cookies for the main domain, bypass Content Security Policy (CSP), or steal sensitive data via browser storage as seen in the ReadMe case. The potential for second-order effects is often missed.
- Bypassing Security Protocols: Attackers can undermine strong authentication (OAuth/SSO) or email security (DMARC/SPF) if a relevant subdomain is compromised, exploiting gaps between different security systems (DNS, cloud, email, web apps).
- Cost Perception Mismatch: Fixing a dangling DNS record is often trivial and free. This perceived ease of remediation leads to deprioritization. However, the potential damage from an exploit can run into millions, creating a dangerous asymmetry between fix cost and potential breach cost. Varying bug bounty valuations ($500 vs. critical P1) also sent mixed signals, though the consensus is shifting towards recognizing the high impact.
- Supply Chain Blind Spot: It's an infrastructure trust issue, not a typical software dependency risk, so it often falls outside standard supply chain risk assessments.
🛡️Building Your Defenses: Monitoring and Mitigation Strategies
Fortunately, awareness and tooling have improved significantly. Effective defense involves a multi-layered approach:
- Continuous Monitoring (Internal & External):
- Attack Surface Management (ASM) Tools: Services like Wiz, Project discovery, Palo Alto Networks Cortex Xpanse, Detectify, Assetnote, and CyCognito continuously scan internet-facing assets, including subdomains, specifically looking for dangling DNS records and signs of takeover. Wiz, for instance, checks cloud DNS configurations (like Route53) daily for pointers to non-existent resources.
- Recommended solutions
- WIZ : Wiz provides a functionality called Security Control Graphs, which enables you to define rules for:
- New Potential Subdomain Takeovers
Dangling DNS records
It detects these issues across all the cloud-native solutions you have integrated with Wiz. It also allows you to configure automation rules, such that whenever a new domain is identified under those rules, it can automatically trigger an IRA ticket creation or send an alert to a specified Slack channel or other destination. Wiz continuously monitors the assets, which helps to identify the issue well before researchers do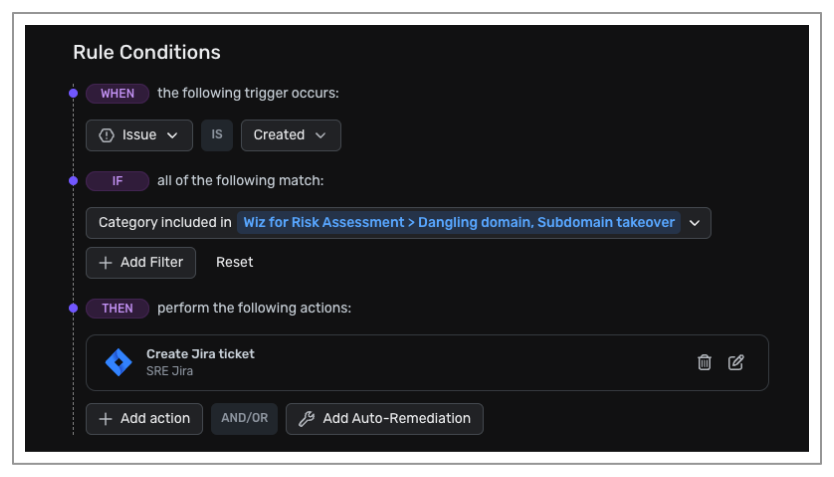
- Project discovery : The Project Discovery SaaS platform offers continuous discovery and scanning functionality. This enables users to configure a process such as:
- Performing asset discovery every 6 or 12 hours.
Following that, conducting a continuous subdomain takeover template-based scan of all assets within a selected asset group.
It also allows for the integration of email notifications, which helps organizations establish proactive monitoring.
- WIZ : Wiz provides a functionality called Security Control Graphs, which enables you to define rules for:
- Recommended solutions
- Attack Surface Management (ASM) Tools: Services like Wiz, Project discovery, Palo Alto Networks Cortex Xpanse, Detectify, Assetnote, and CyCognito continuously scan internet-facing assets, including subdomains, specifically looking for dangling DNS records and signs of takeover. Wiz, for instance, checks cloud DNS configurations (like Route53) daily for pointers to non-existent resources.
These are cost-effective modern tools. If you are seeking automation for continuous subdomain posture monitoring, I highly recommend setting up SubSpy: https://github.com/themalwarenews/SubSpy.
SubSpy can be configured to:
- Scan assets using Subfinder.
- Scan for vulnerabilities using Nuclei( Takeover template).
- It can be hosted on any instance and scheduled as a cron job to perform automated discovery and send alerts to Discord, Slack, or a source of your choice. To enhance asset discovery, I would recommend adding Subfinder API keys.

- Leverage Cloud Provider Safeguards:
- Domain Verification: Many platforms (GCP DNS Services, Heroku, GitHub Pages) now require DNS-based verification (e.g., TXT records with unique tokens like
asuid) before a custom domain can be used, preventing malicious claims. - Integrated DNS Records: Use features like Azure DNS alias records, which link directly to Azure resource IDs and can update automatically if the resource is deleted.
- Platform Policies: Providers like Heroku automatically release custom domains upon app deletion, and some prevent re-registration of sensitive names.
- Domain Verification: Many platforms (GCP DNS Services, Heroku, GitHub Pages) now require DNS-based verification (e.g., TXT records with unique tokens like
- Implement Strong DNS Hygiene Policies:
- Regularly audit DNS zones for stale CNAME, A, or MX records pointing to external services no longer in use.
- Remove unused subdomains promptly.
- Consider using wildcard DNS records cautiously, as misconfigurations can be catastrophic.
- Heed Government and Industry Guidance:
- Follow recommendations from bodies like CISA (Directive 19-01), NCSC (UK), and NIST (SP 800-172), which emphasize DNS security and asset management.
- Participate in coordinated vulnerability disclosure programs (e.g., via HackerOne) to benefit from ethical hacker findings.
- Configure Security Protocols Correctly:
- Ensure DMARC policies cover subdomains appropriately.
- Carefully manage OAuth
redirect_urilists, removing URIs pointing to decommissioned subdomains. - Scope session cookies as narrowly as possible.
Conclusion
Subdomain takeovers represent a tangible and ongoing threat fueled by the complexity of modern cloud infrastructure and gaps in asset management. Attackers actively exploit these weaknesses for phishing, data theft, session hijacking, and more. While the fix for a single dangling record might be simple, preventing the issue requires continuous vigilance, robust processes, and leveraging modern security tools and platform features. By treating DNS hygiene as a critical security function, organizations can close this often-overlooked door and significantly reduce their risk exposure in today's threat landscape.


